Missing Function Level Access Control (FLAC) – With Examples

Data security is a critical element of any modern application. For this reason, it’s important to implement access control measures that ensure only authorized individuals can have access to data. One of the more commonly used access control measures is known as Function Level Access Control (FLAC).
Let’s first review what is Function Level Access Control before delving into the impacts of this vulnerability on an application’s security posture, followed by practical steps for mitigating these risks in production systems.
What is Missing Function Level Access Control?

A missing function-level access control (FLAC) vulnerability occurs when a web application fails to properly restrict user access at the functionality level. This allows unauthorized users to access areas of an application, view confidential information, and make changes to data that they should not be able to see or change. Attackers can exploit such vulnerabilities by using a variety of methods, including manipulating parameters in the URL or using SQL injection.
Example of MFLAC
Assume that User A logs into an online banking account and then clicks on the “Transaction History” page without being prompted for authentication again. If this page does not have appropriate FLAC controls, then another user with no authorization can simply use the same URL (or manipulate parameters) and gain access to User A’s entire transaction history without providing any credentials.
Check How To Prevent Unauthorized Computer Access.
How Can Attackers Exploit the FLAC Vulnerability?
The prying eyes/attackers use following methods to exploit FLAC vulnerability:
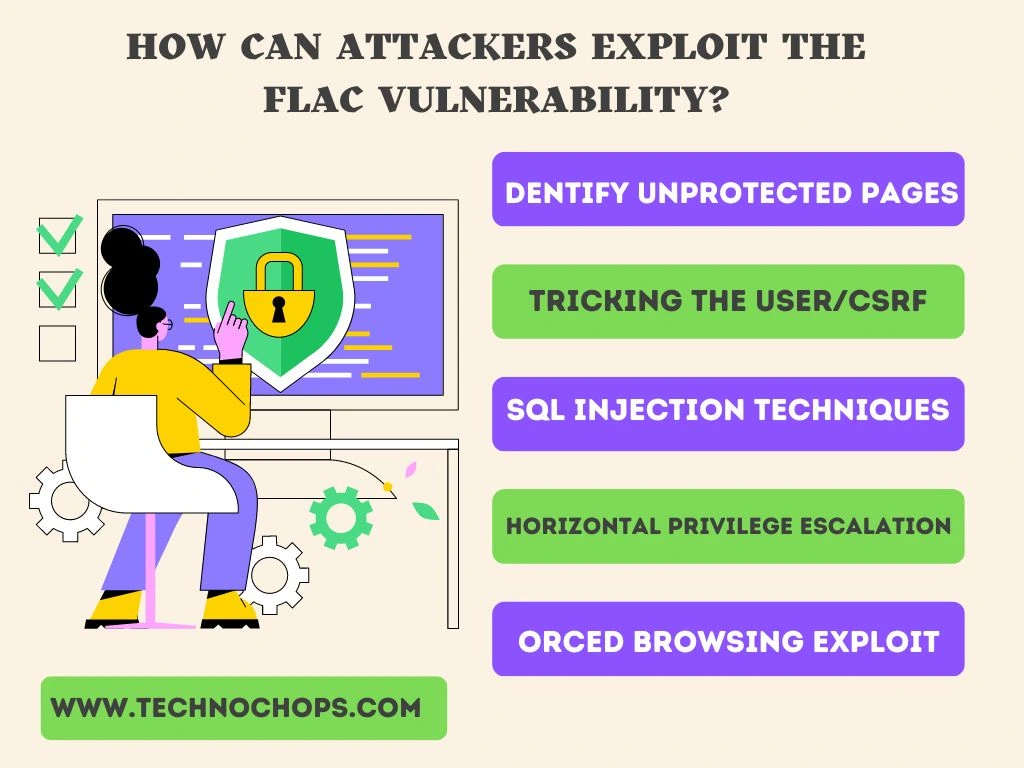
1. Identify Unprotected Pages
Attackers can exploit FLAC vulnerabilities by identifying pages that do not secure access as they should. They may also craft malicious URLs which contain specific parameter values to bypass authentication steps, allowing them unrestricted access to sensitive sections of web applications that wouldn’t normally allow it by design.
2. Tricking the User/CSRF
Attackers may take advantage of cross-site request forgery (CSRF), which involves tricking a logged-in user into performing certain actions on behalf of the attacker such as changing a password or transferring money from one account to another.
3. SQL INJECTION TECHNIQUES
Some attackers may try various SQL injection techniques in order to bypass authentication restrictions that are set up within database servers like Oracle or Microsoft SQL Server by injecting malicious code directly into queries sent from web browsers; making it possible for them to get around existing security measures set up by software developers and gain unrestricted access over sensitive information stored inside corporate databases or other back-end systems connected directly via API calls made from vulnerable web applications.
4. Horizontal Privilege Escalation
It is a type of attack in which an attacker takes advantage of vulnerabilities found in access control systems to gain unauthorized access to user accounts. This kind of attack exploits the fact that these control systems are typically based on user IDs, which attackers can modify in order to gain access.
Example
A good example of it is the attacker logging into a website using their own account and URL parameters including the user’s ID.
A malicious actor can modify the UID parameter after authentication and log into other users’ accounts without authorization. In this case, if someone has logged into http://darwin.com/app/uID=1738, they could potentially be able to change it to http://darwin.com/app/uID=3225 and logging in as another application user simply by altering the string at the end of the URL address bar.
5. Forced Browsing Exploit
Another method commonly used by attackers is Forced Browsing Exploit which involves hackers attempting to discover obscured URLs that contain sensitive information or admin functions within web applications via trial-and-error techniques like brute forcing or simple guessing strategies!
Let us take the same Darwin example!
how to protect against missing function level access control
Protecting against FLAC vulnerability is necessary. You can employ the following methods to save yourself from the aftermath of the attack!

1. enforce the law of least privilege
This requires that users are only assigned privileges and roles in order for them to complete their tasks and no more.
For example, a sales employee should not be able to access payroll information or any other sensitive data within their system as it is outside their job description.
By limiting user access control, organizations can ensure that users are accessing exactly what they need while keeping all other sensitive data safe from unauthorized access.
2- Checkout User Logs
Another method organizations can use to prevent missing function level access control is through logging events related to the user’s activity within the system. This allows administrators or security personnel to review activity logs and detect suspicious activities such as a user trying to perform distinct functions than allowed by their assigned role or attempting actions that go beyond typical user behavior expectations for that particular role type.
Organizations can also ensure all log files are monitored at regular intervals so any abnormal changes will be detected quickly before it has a chance of violating security policies associated with function-level permissions.
3- Role-Based Access Control (RBAC)
Using RBAC is also an effective way for organizations to manage employee functions at the business level in order to reduce potential violations of missing function levels from occurring. This mechanism groups users into distinct roles, defining what types of tasks they can complete based on departmental needs and limiting modifications they may make regarding certain systems or documents based on predetermined criteria set out by management teams during implementation process stages.
As well, RBAC systems support multiple layers of permissions allowing managers greater flexibility when assigning different sets of specific task objectives across various areas while keeping track overall hierarchy securely throughout each organization’s network environment.
The advantages gained by implementing RBAC includes.
Check Difference Between Intranet And Extranet.
Wrapping It Up
In conclusion, missing function-level access control is a serious security risk and should be prevented at all costs. Access to important system functions must be monitored and restricted to ensure that only authorized users can perform privileged actions on the system while still allowing them to carry out their necessary work. Best practices such as role-based access control or privilege management systems can help organizations ensure that these risks are minimized and protect the data they store.