Data Masking Vs Encryption: The Best Option in 2023?
Your data is end-to-end encrypted’ or ‘Your data is masked’ are the expressions you have been seeing on several sites, applications, receipts, bank forms, and sale demos. Ever wondered what they mean?
Data masking and encryption are two important methods to protect or secure your data from cyber threats and online scams.
With the technology advancement, there are incalculable techniques to secure your data together with data masking and encryption.
But the real question arises: What’s the difference between data masking vs encryption? Besides, are you using the right tool to protect your data?
Many people confuse data masking with encryption and even consider them the same. If you also think so, then no worries.
Because this article will cover the clear difference between data masking and encryption plus the best option amidst them.
Let’s start with their brief description:
What Is Data Masking?
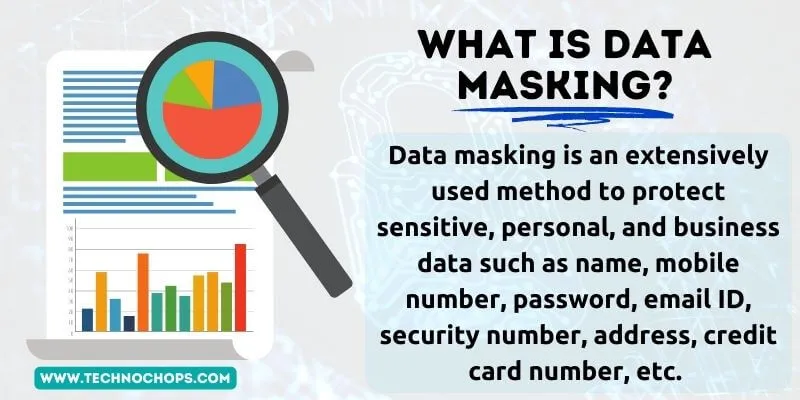
Also known as data obfuscation, data masking is a way to protect sensitive data by disguising the real data into a masked one. A functional alternative to your data is created and the real data is kept secure.
Data masking is an extensively used method to protect sensitive, personal, and business data such as name, mobile number, password, email ID, security number, address, credit card number, etc.
Data masking tools are available in the market that ‘mask’ your data with such proficiency and maintains its utility. The data masking software tools replace the original data characters with some random or fictional characters.
In short, data masking is a practicable method to let firms use your data without revealing the real data.
Check Advantages And Disadvantages of Peer-To-Peer Networking
Types of Data Masking
Data can be masked by these major methods:
1- Static Data Masking
In static data masking, data is masked and another copy of it (with disguised data) is made. This copy is then at rest rather than in active use. This method is acknowledged when data is available only for one-time use.
2- Dynamic Data Masking
In dynamic data masking, data is masked and kept linked with the source. It is kept active and is the most secure type of data masking.
3- Deterministic Data Masking
It is the process of masking the data by replacing it with the same values in a repeatable way.
4- Data Scrambling
The sensitive data is scrambled randomly to obfuscate it.
5- On- the-fly Data Masking
It is a method to transfer smaller subsets of data to other environments such as testing or research.
6- Nulling Out
The masking of data by replacing a real value or character with a null one.
7- Substituting
To substitute the real data with some fake but authentic data.
What Is Encryption?

Encryption is a method by which you can convert real data (plaintext) into encrypted data (cyphertext) with the aid of encryption algorithms. This encrypted data if hacked or stolen proves legitimately futile.
However, the encrypted data can be again converted to real data by using a specialized decryption key to serve its purpose.
Data encryption has been considered a remarkable method to protect data because of its reversibility feature i.e., the data can be restored to its original form by using the encryption key.
Data can therefore be preserved without any potential risks of unauthorized access or damage. You might Check Broadband vs Narrowband
Types of Data Encryption
There are two methods of data encryption that are used widely:
1- Symmetric Encryption
The encryption and decryption both use the same key. To put it another way, encryption and decryption can be accessed through a single key. One key is used by the sender and recipient to encrypt or decrypt the data.
2- Asymmetric Encryption
Encryption and decryption use two different keys viz. public and private keys. A public key is used to encrypt the data and can be accessed by a group of people. Whereas, a private key is the decryption key and is only used by the owner.
Key Differences: Data Masking vs Data Encryption
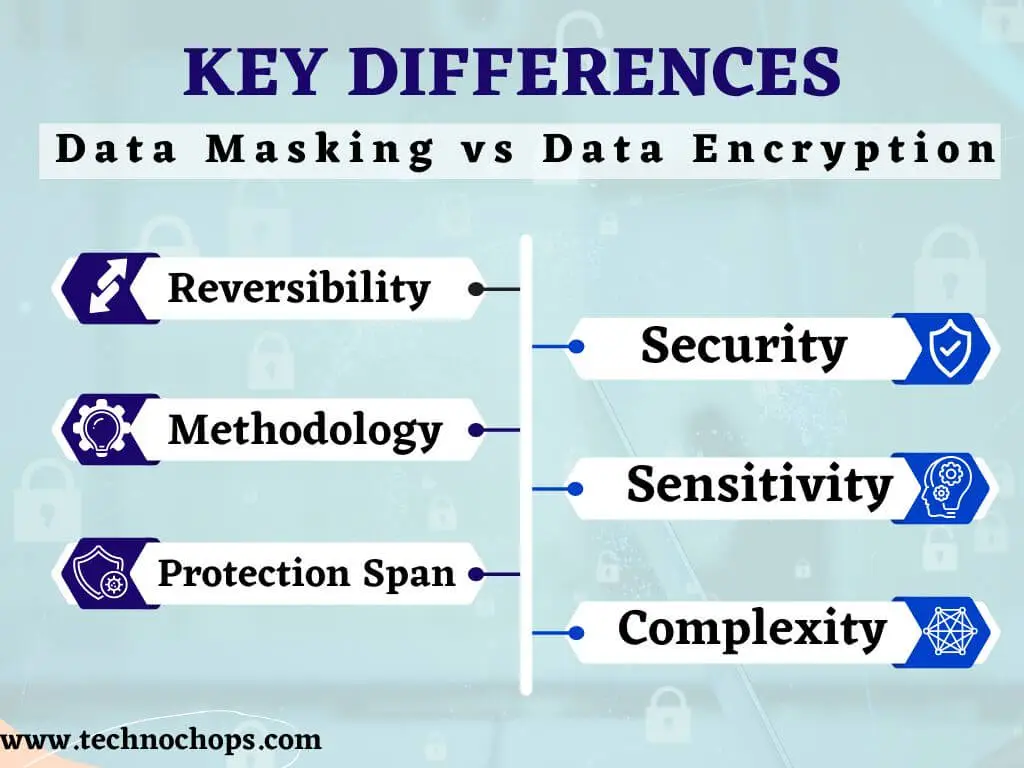
1- Reversibility
Encrypted data is reversible data since it can come to its real form. The encrypted data can be decrypted by using the key.
The masked data is irreversible and once masked it cannot be availed in its real form.
2- Security
In terms of security, data masking takes the lead. Since once the data is masked it becomes completely useless to any potential loss.
However, in the case of encrypted data, there can be a chance for the decryption key to go into the wrong hands resulting in data loss.
3- Methodology
Data masking protects the data by camouflaging the original data with another set of fake data.
Encryption does so by altering the real data with various algorithms that can be decrypted using a key.
4- Data Sensitivity
Working in a big firm and dealing with sensitive data, masking is preferred. Since it offers a high-security rate.
If non-sensitive data is to be preserved from unauthorized access, then encryption is used.
5- Protection Span
Data encryption is used to protect the data for long-term use since it can be converted into original data or encrypted data using a key.
Data masking is usually for short-term use as once the data is masked it cannot be restored.
6- Complexity
Data encryption is considered a more complex method than data masking. Encryption conducts with complex algorithms and uses a decryption key over time. Whereas masking is easy to handle since the masked data is ever functionally available. you may like LAN vs WAN Port
Wrapping Up: Data Masking vs Data Encryption
Data masking and encryption both are standard methods of securing the data. In the data privacy world, both ways protect the risks of data being exposed.
However, the best option for you depends upon the type of data you are protecting and the methodology you feel ease at with.
In conclusion, data masking and encryption both have their benefits and drawbacks as well. Whichever, the method you select, you should put effort to prevent data exposure.
Which data protection way do you find better? Let us know in the comments below.